In order to configure your LDAP connectivity, you will need to set the LDAP parameters in const.php. This article will show you how to set them properly using the UI for Config Variables.
2. Establishing a Сonnection to the LDAP Server
You will need to know the type of directory server you are using; i.e., OpenLDAP or Windows ActiveDirectory.
The minimum parameters needed to be set in the config variables are:
- URL of LDAP Server
- LDAP Server username and password if required
- LDAP_BIND_REQUIRES_DN for OpenLDAP only
- BaseDN
These settings may be edited by clicking on the edit icon (gear) for each item.
By setting these parameters correctly, you will be able to authenticate against LDAP. The remaining parameters are to synchronize User information and are explained in Step 3.
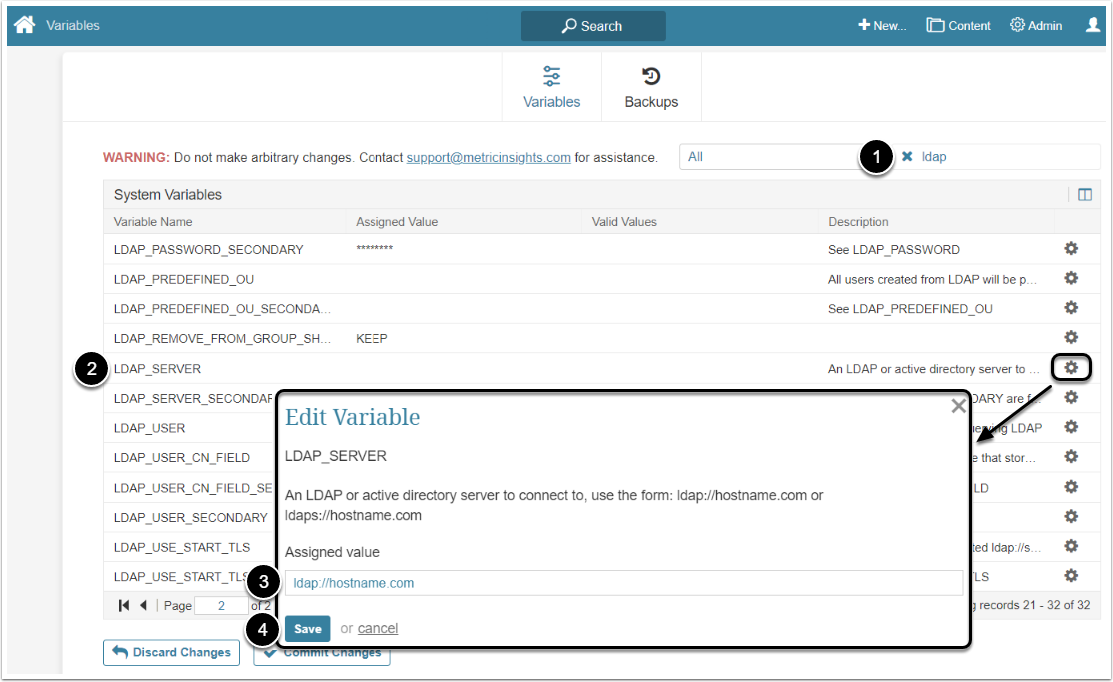
2.1. LDAP Server
- Filter the Variable by "ldap"
- Find the "LDAP_SERVER" Variable and click the gear icon in its row
- Assigned value: Type the server active directory address
- [Save]
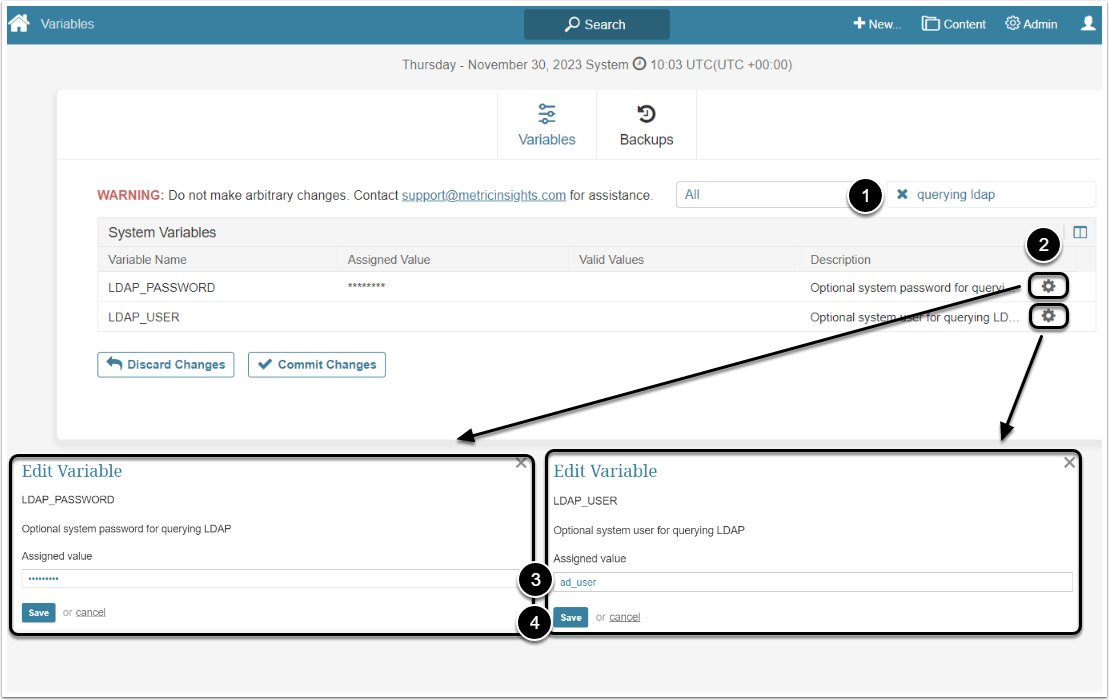
2.2. LDAP Username and Password
If your LDAP server requires a username and password to query the directory, set LDAP_USER and LDAP_PASSWORD accordingly.
- Filter the Variable by "querying ldap"
- Click the gear icon to open the pop-up
- Assigned value: Type the Username and Password
- [Save]
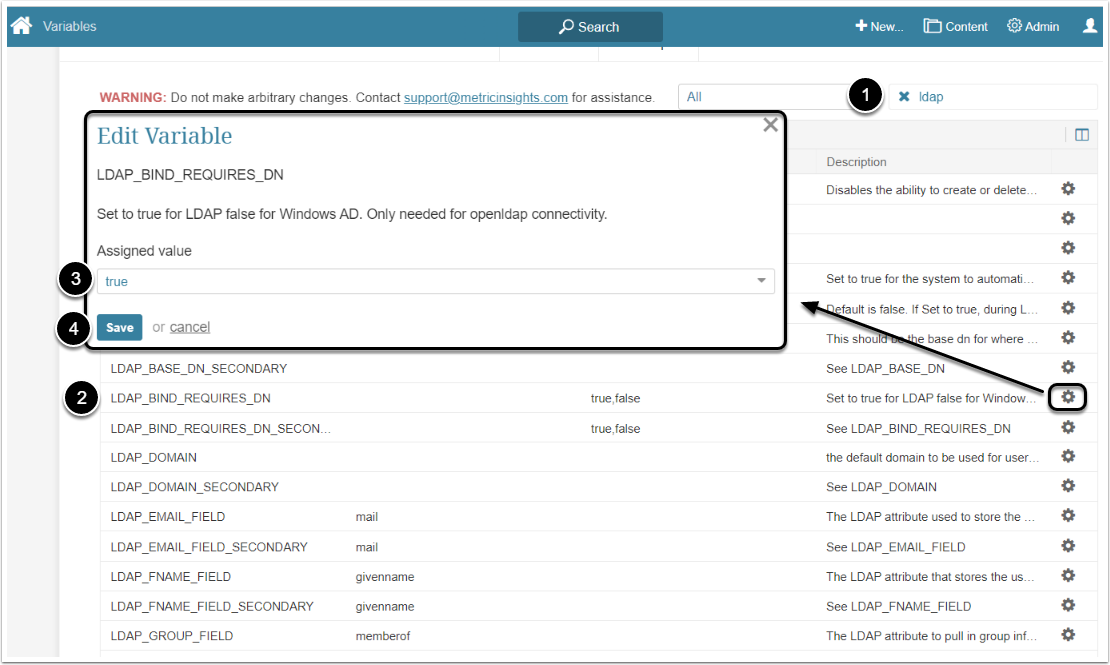
2.3. LDAP Bind Requires DN
If you are using an OpenLDAP server, sometimes you can't authenticate as user@domain, but instead, need to authenticate as uid=user,dc=example,dc=com. If this is the case, set "LDAP_BIND_REQUIRES_DN" to 'true'. Otherwise, leave this as false.
- Filter the Variable by "ldap"
- Find the "LDAP_BIND_REQUIRES_DN" Variable and click the gear icon in its row
- Assigned value: Select "true" option
- [Save]
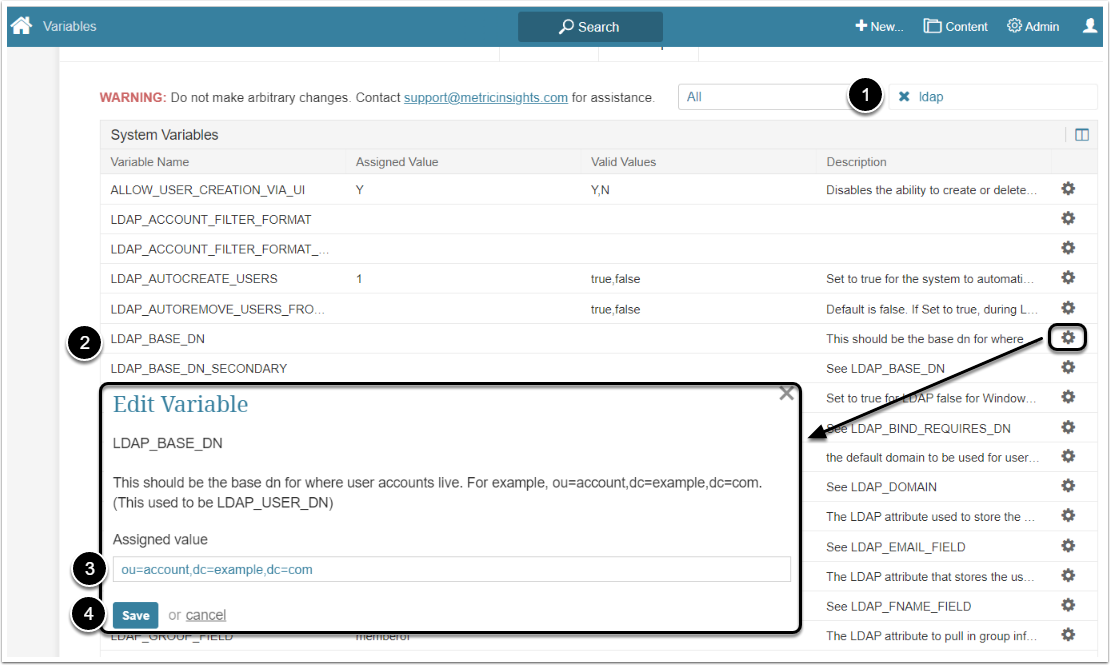
2.4. LDAP Base DN
- Filter the Variable by "ldap"
- Find the "LDAP_BASE_DN" Variable and click the gear icon in its row
- Assigned value: Base DN needed to query to login to. For example, if your username is uid=user,ou=useraccounts,dc=metricinsights,dc=com, then the BaseDN would be ou=useraccounts,dc=metricinsights,dc=com
- [Save]
3. Synchronizing User data
After you have successfully authenticated, Metric Insights needs to know a few more things about your LDAP user schema so we can properly sync information with the corresponding Metric Insights user. This can be done by setting the following parameters:
- LDAP_USER_CN_FIELD
- LDAP_EMAIL_FIELD
- LDAP_FNAME_FIELD
- LDAP_LNAME_FIELD
These should point to the corresponding LDAP field names.
Finally, if you have a failover LDAP server, you will need to repeat these steps and setup the corresponding LDAP_*_SECONDARY parameters to work for your failover LDAP server.
Be certain to [Commit Changes] to update the file.
4. OpenLDAP Example
- dn: uid=testuser,ou=people,dc=metricinsights,dc=com
- uid: testuser
- uidNumber: 1001
- gidNumber: 1000
- cn: testuser
- sn: Test
- objectClass: top
- objectClass: person
- objectClass: inetOrgPerson
- objectClass: posixAccount
- objectClass: shadowAccount
- loginShell: /bin/bash
- homeDirectory: /home/testuser
- givenName: Foopie
- mail: foopie@foo.com
In this case,
- LDAP_USER_CN_FIELD = 'uid'
- LDAP_EMAIL_FIELD = 'mail'
- LDAP_FNAME_FIELD = 'givenName'
- LDAP_LNAME_FIELD = 'sn'
5. "User authenticated via" Field
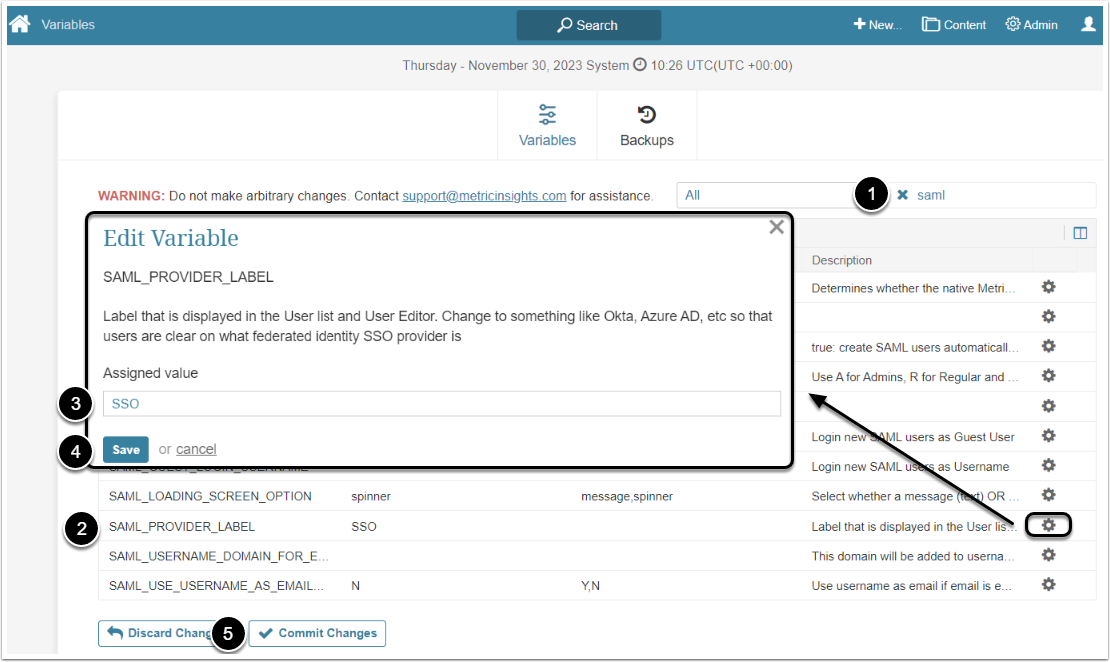
In 6.4.4 version a new Variable "SAML_PROVIDER_LABEL" is added. This Variable defines the label that is displayed in the User list (in the Auth column) and User Editor (in the User authenticated via field).
- Filter the Variable by "saml"
- Find the "SAML_PROVIDER_LABEL" Variable and click the gear icon in its row
- Assigned value: The default value is SSO, change it if there is different provider
- [Save]
- [Commit Changes]