Metric Insights is compatible with OpenID authentication. This article describes required steps that an Administrator must perform to configure Metric Insights for use with OpenID connect.
In this article, Microsoft Azure will be used as an example Identity Provider.
1. Register an App in the Identity Provider Account
1.1. Start a New App Registration
- Open Azure Portal and log into account.
- Access App registrations tab.
- [+ New registration] to register an application.
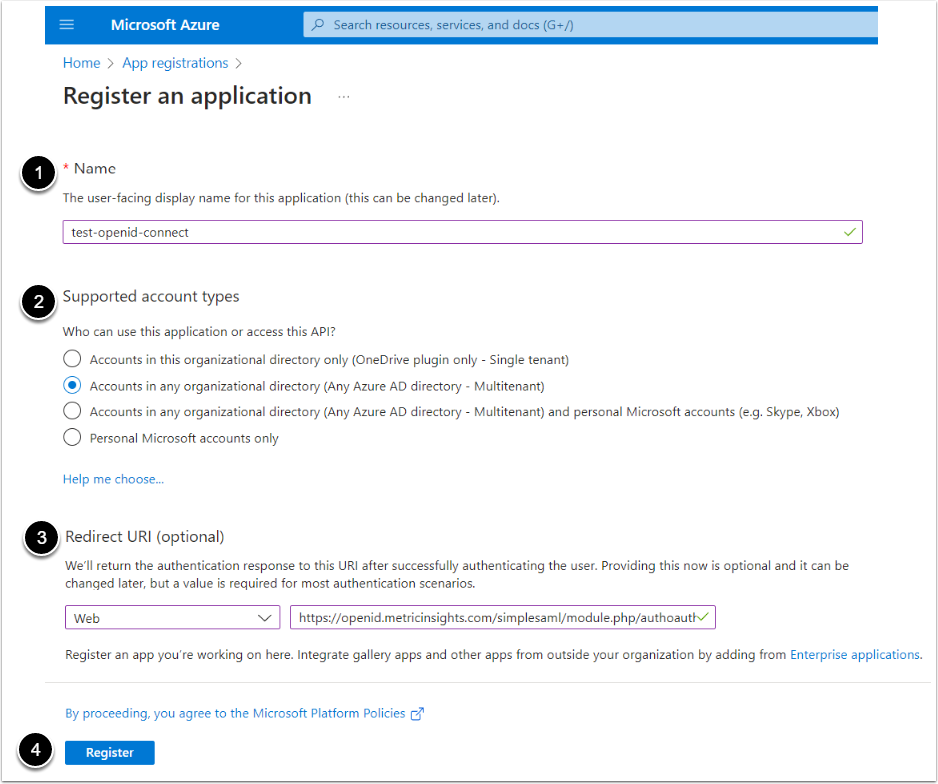
1.2. Complete the Registration
- Name: Give the application a descriptive name.
- Supported account types: Select an "Accounts in any organizational directory (Any Azure AD directory - Multitenant)" option.
- Redirect URI: In the left dropdown menu choose "Web" option and type into the right field type the redirection URI in the following format:
https://<MI hostname>/simplesaml/module.php/authoauth2/linkback.php - [Register]
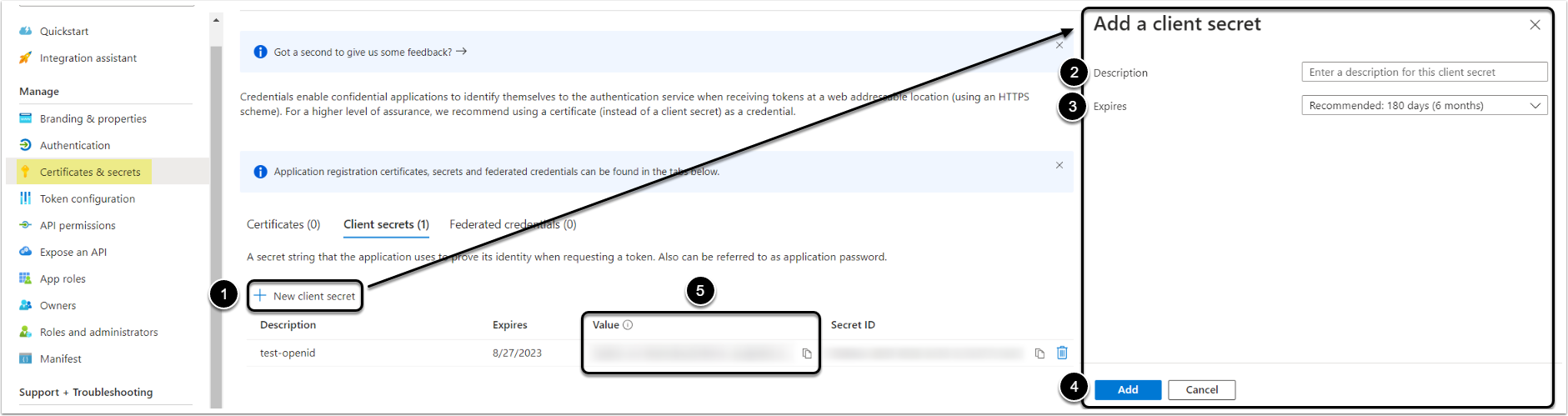
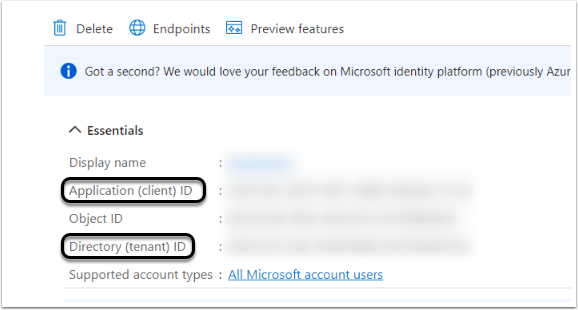
- For further steps copy the following IDs:
- Application (client) ID;
- Directory (tenant) ID.
2. Configure Metric Insights from SSH Terminal (PuTTY)
Open a terminal using SSH or PuTTY and access the Metric Insights instance
The next steps:
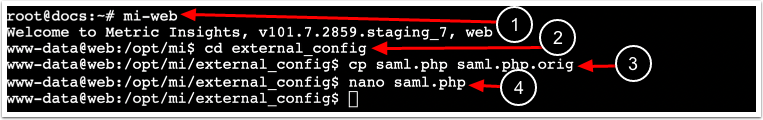
- Enter the
webdocker container.
- For Simple Installation use
mi-web
- Change directory to
/opt/mi/external_config:
cd /opt/mi/external_config- Make copy of the current
saml.php:
cp saml.php saml.php.orig- Open
saml.php:
- For MI v7:
nano saml.php- For MI v6:
vi saml.php- Paste the following content and update appropriate values regarding OpenID configuration:
Metric Insights v7:
OpenID Connect v2 example:
<?php
define('SAML_SIGNING_KEY', '/opt/mi/ssl/server.key');
define('SAML_SIGNING_CERT', '/opt/mi/ssl/server.crt');
define('SAML_SIGN', FALSE);
define('SAML_ENCRYPT', FALSE);
define('SAML_ADMIN_PASSWORD', '********');
define('SAML_AUTH_SOURCE', 'openidconnect');
define('SAML_URL_ISSUER', 'https://login.microsoftonline.com/<TENANT ID>/v2.0');
define('SAML_CLIENT_ID', '<CLIENT ID>');
define('SAML_CLIENT_SECRET', '<SECRET ID>');
define('SAML_URL_REDIRECT_URI', 'https://<METRIC INSIGHTS INSTANCE URL>/oauth2/idpresponse');
define('SAML_DISCOVERY_URL', 'https://login.microsoftonline.com/<TENANT ID>/v2.0/.well-known/openid-configuration');
define('SAML_UID_FIELD', 'id_token.preferred_username');
define('SAML_EMAIL_FIELD', 'id_token.preferred_username');
define('SAML_FNAME_FIELD', 'given_name');
define('SAML_LNAME_FIELD', 'family_name');Metric Insights v6:
- OpenID Connect v1 example:
<?php
define('SAML_ADMIN_PASSWORD', '********');
define('SAML_SIGNING_KEY', '/opt/mi/ssl/server.key');
define('SAML_SIGNING_CERT', '/opt/mi/ssl/server.crt');
define('SAML_SIGN', FALSE);
define('SAML_ENCRYPT', FALSE);
define('SAML_AUTH_SOURCE', 'openidconnect');
define('SAML_URL_ISSUER','https://sts.windows.net/<TENANT ID>/');
define('SAML_CLIENT_ID','<CLIENT ID>');
define('SAML_CLIENT_SECRET','<SECRET ID>');
define('SAML_DISCOVERY_URL','https://login.microsoftonline.com/<TENANT ID>/v2.0/.well-known/openid-configuration');
define('SAML_UID_FIELD', 'name');
define('SAML_EMAIL_FIELD', 'unique_name');
define('SAML_FNAME_FIELD', 'given_name');
define('SAML_LNAME_FIELD', 'family_name');- OpenID Connect v2 example:
<?php
define('SAML_ADMIN_PASSWORD', '********');
define('SAML_SIGNING_KEY', '/opt/mi/ssl/server.key');
define('SAML_SIGNING_CERT', '/opt/mi/ssl/server.crt');
define('SAML_SIGN', FALSE);
define('SAML_ENCRYPT', FALSE);
define('SAML_AUTH_SOURCE', 'openidconnect');
define('SAML_URL_ISSUER','https://login.microsoftonline.com/<TENANT ID>/v2.0');
define('SAML_CLIENT_ID','<CLIENT ID>');
define('SAML_CLIENT_SECRET','<SECRET ID>');
define('SAML_DISCOVERY_URL','https://login.microsoftonline.com/organizations/v2.0/.well-known/openid-configuration');
define('SAML_UID_FIELD', 'name');
define('SAML_EMAIL_FIELD', 'id_token.preferred_username');
define('SAML_FNAME_FIELD', 'given_name');
define('SAML_LNAME_FIELD', 'family_name');Replace <TENANT ID> with the Directory (tenant) ID, <CLIENT ID> with the Application (client) ID and <SECRET ID> with Secret ID Value gathered in the Identity Provider's account.
NOTE: In this example we use Microsoft Azure, but other Identity Providers will provide different SAML_URL_ISSUER and SAML_DISCOVERY_URL. Your specific fields – SAML_UID_FIELD, SAML_EMAIL_FIELD, SAML_FNAME_FIELD, SAML_LNAME_FIELD, etc. – can also be different.