This article covers the Metric Insights' Security Model best practices for new customers using a single sign-on application. The common workflow is as follows:
Customer prerequisites:
- Identify those users who need accounts in Metric Insights and determine User Type.
- Determine potentials Groups, Categories, and Elements required by each User Type.
- If needed, request that a new LDAP group be created.
- Designate an early adopter organization and integrate with MI using mi-ldap-usersync.
1. Sync Groups from LDAP/AD
The recommended approach is to begin by syncing LDAP/AD groups and users via the mi-ldap-usersync script.
Find instructions in this article.
The script syncs groups and users in those Groups first versus syncing individual Users. The process is as follows:
- The script adds external groups to Metric Insights along with their assigned users and preserves the exact same group naming.
- If a user in a group that is being synced does not yet exist in Metric Insights, the User will be created in MI, if required.
- If not specified in the --user-type parameter, the User is created as Regular User without any Privileges or Permissions. Only informational data for the User's profile, along with its assigned Group is included: user ID, email address, first name, and last name.
Best practice: Sync groups from your identity provider.
For user creation, you have the following options:
| Method | Account is created | Source of group membership | Key behavior | Typical use case |
| LDAP Sync | Before the user ever logs in | Active Directory or O365 group membership | The LDAP sync job periodically scans specified AD/O365 groups and automatically creates accounts in Metric Insights for all matching members. These accounts exist and are group-assigned even if the user has never signed in. | Ensures all required users are ready in the system ahead of time, often for controlled rollouts, distributions/Bursts, or pre-assigned ownership. |
| SAML on first login | At user’s first successful sign-in | Active Directory or O365 group membership | When the user logs in through SAML for the first time, Metric Insights automatically creates their account and assigns them to groups based on the mapping returned from LDAP sync. | Best for just-in-time provisioning, where you don’t need accounts until users actually log in, reducing unused accounts. |
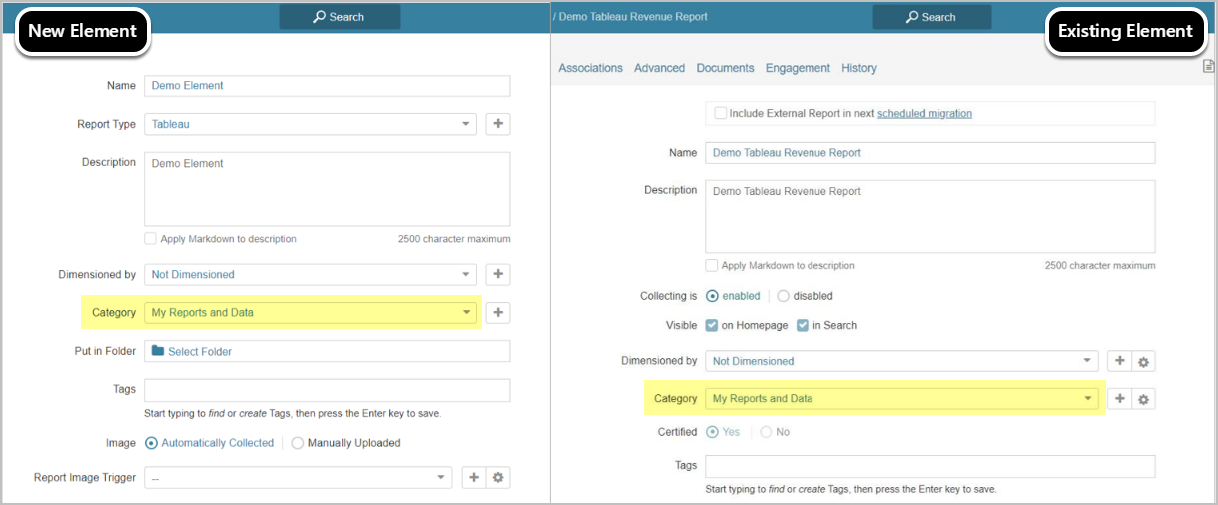
2. Create Categories and Assign Elements to Them
Next, create Categories. Categories are used to group content by topics or roles and responsibilities of those using them.
Elements can be assigned to the default Uncategorized Category, but we strongly recommend that content be assigned to a relevant Category to avoid unauthorized access to data.
- When creating new Elements, assign them to relevant Categories.
- Existing Elements can be moved between Categories as needed.
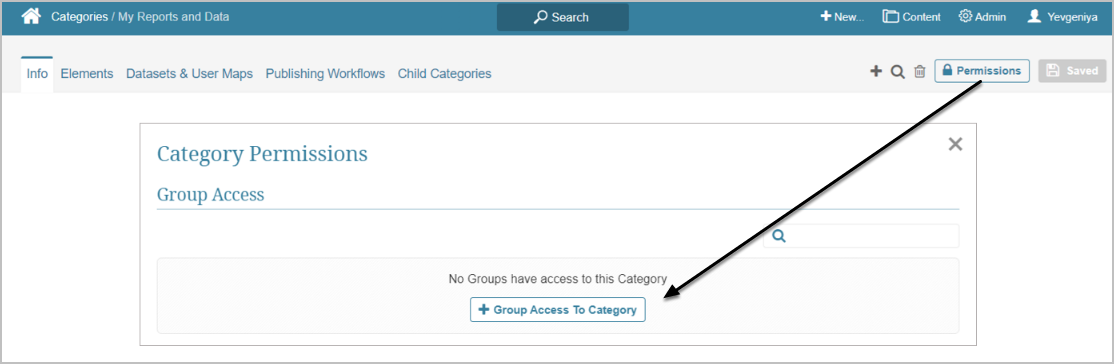
3. Assign Groups to Categories
Assign the Groups to Categories based on the content to which the members require access.
- Categories are also a way to provide access to the content only to Groups and Users with Permission to View or Edit the Category and/or its content.
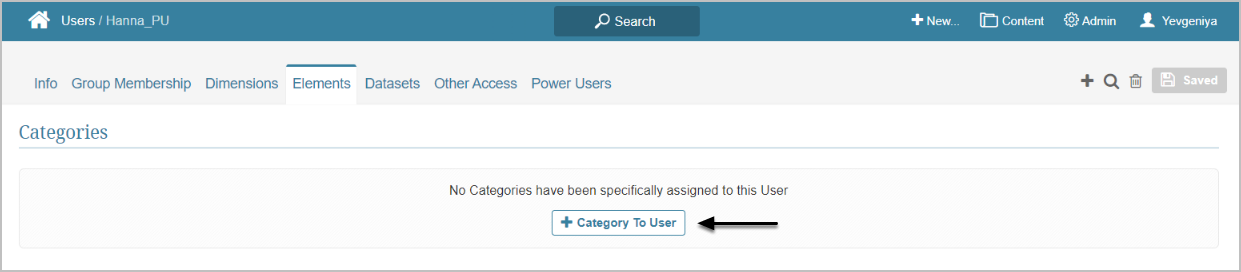
- Permissions can be granted from either Category, Group, or individual User editors.
OR
OR (alternatively)
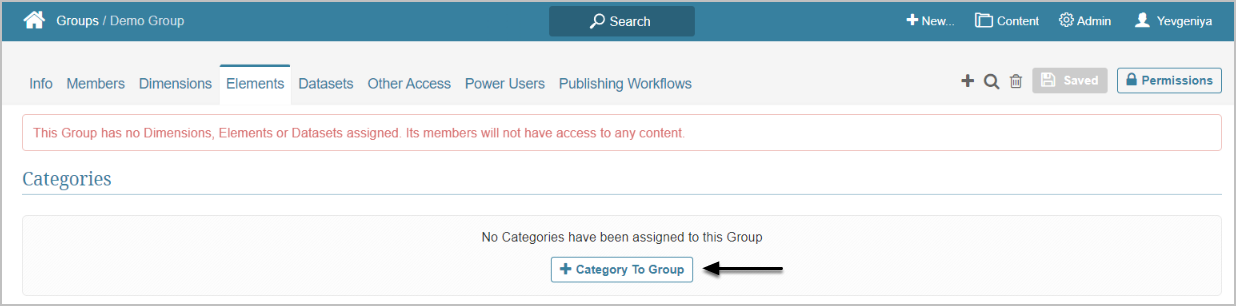
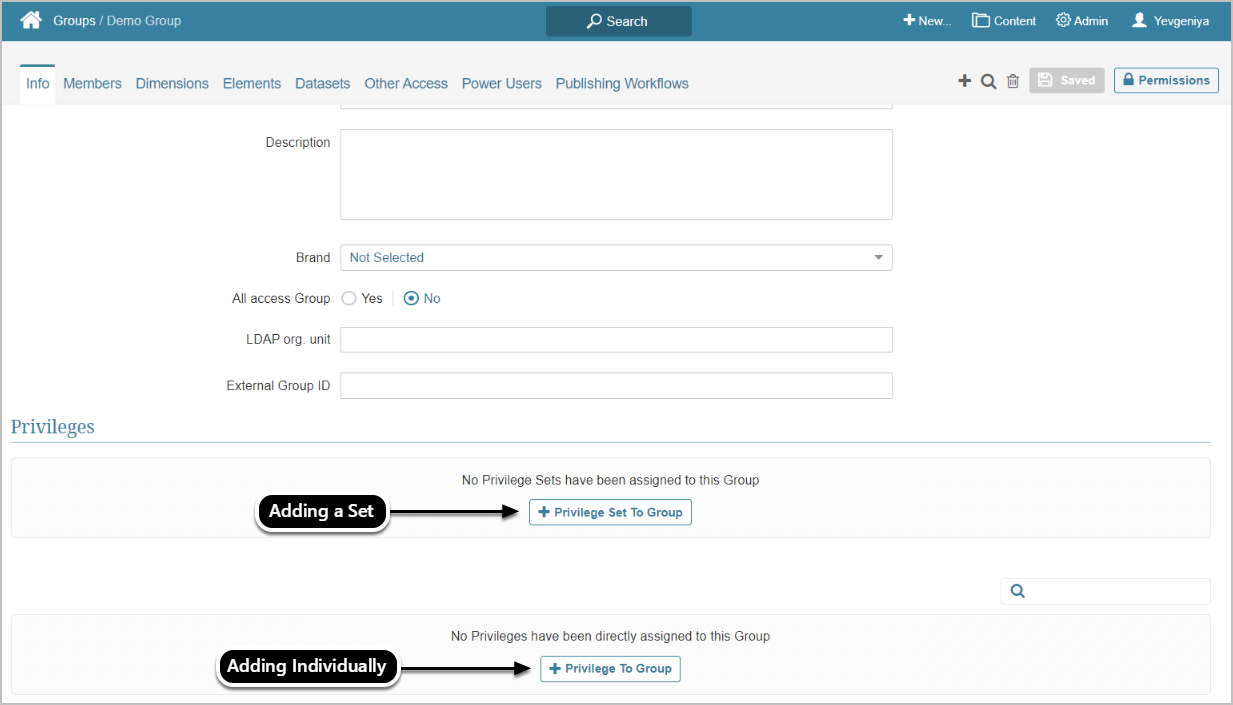
4. Assign Privileges to Groups
Assign necessary Privileges to Groups to control whether or not Users within the Group can use certain features and/or and set selected personal Preferences.
Privileges assigned to a Group are inherited by all Group members. You can assign Privileges based on Privilege Sets or individually.
For more information on maintaining Group security, refer to this article.
4.1. Decide How to Manage Power Users/Admins
Extending or limiting capabilities for specific Groups of MI Users is possible via creating custom Groups (outside the AD user sync). You can:
- Create a custom Group in AD, sync it with MI, and assign the required Privileges or Privilege Sets. Convenient for maintaining and managing centrally a large Group of Users.
- Create a custom Group directly in MI and assign the required Privileges or Privilege Sets. Convenient for small Groups.
For more information on differences and overlaps between Admin and Power User rights, refer to this article.
4.2. Decide How Security Should Function Relative to Your BI Tools
You can follow one of the two approaches:
-
Mirror access to the content from your BI tools: the system will apply restrictions and limitations that already exist in your BI tools to the content in MI.
- For more information on how to synchronize content access in Tableau with Tableau content that exists in MI, refer to this article.
- Configure content discoverability: you can configure what content Users without access in your BI tools can view in MI.
4.3. Decide How to Manage Access Requests for Content
You can follow one of the two approaches:
- Configure centralized Access Request processing; e.g., via SAP GRC or ServiceNow. The tool can be integrated with Metric Insights to manage access to content across all of your organization's BI tools, including MI.
- Configure distributed Access Request processing on the MI side. Being Metric Insights-specific, this configuration is more lightweight.
5. User Maps for Content Security
- Dimension-Level Security: By applying a User Map to a Dimension, you can control which specific Dimension Values each User or Group is allowed to see. Once configured, the User Map automatically enforces these restrictions across all related Elements—Metrics, Reports, and External Reports—so each User only sees their permitted Dimension Values. For more information, refer to this article.
- Row-Level Security: Implemented via User Maps, restricts data at the row level in the underlying Dataset, granting Users/Groups access only to the rows that match their assigned values. For setup details, refer to this article.