This article details how to integrate Metric Insights with Active Directory Federation Services (ADFS) using the SAML protocol on the ADFS side for user auth.
Configuring ADFS
1. Add Relying Party Trust
Access the ADFS Server > AD FS Management
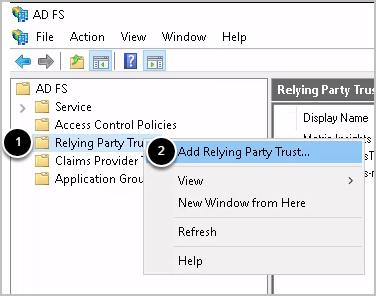
- Right-click Relying Party Trusts
- Select Add Relying Party Trust to launch the Add Relying Party Trust Wizard
1.1. Welcome
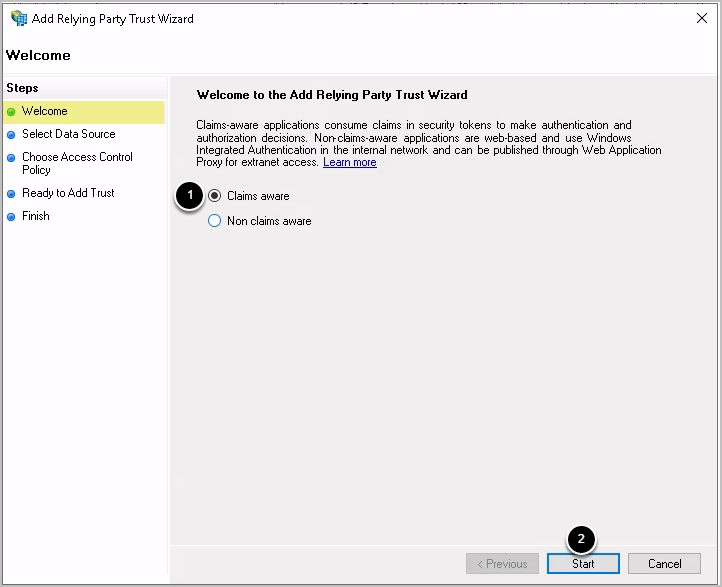
- Choose Claims aware
- [Start]
1.2. Select Data Source
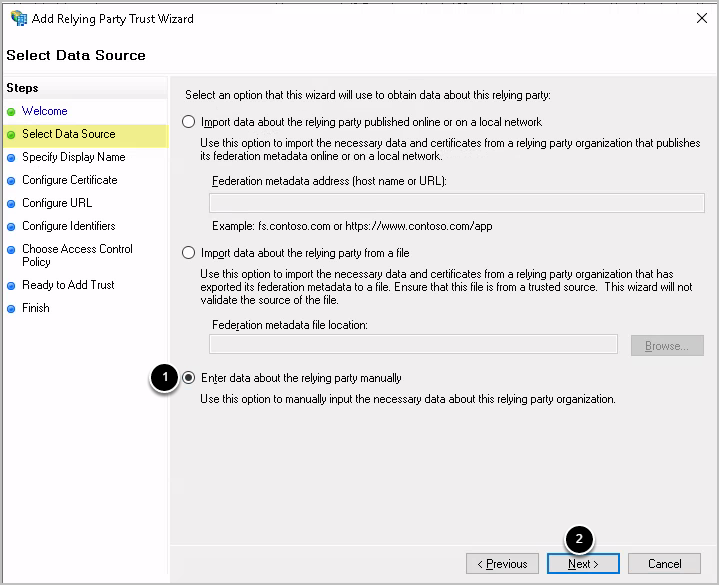
- Select Enter data about the relying party manually
- [Next]
1.3. Specify Display Name
- Specify Display Name
- [Next]
1.4. Configure Certificates
- Click [Next]
NOTE: If you need to configure encryption, it must also be configured on the Metric Insights' side.
1.5. Configure URL
Access the Installation Page for simpleSAML in Metric Insights at https://<hostname>/simplesaml
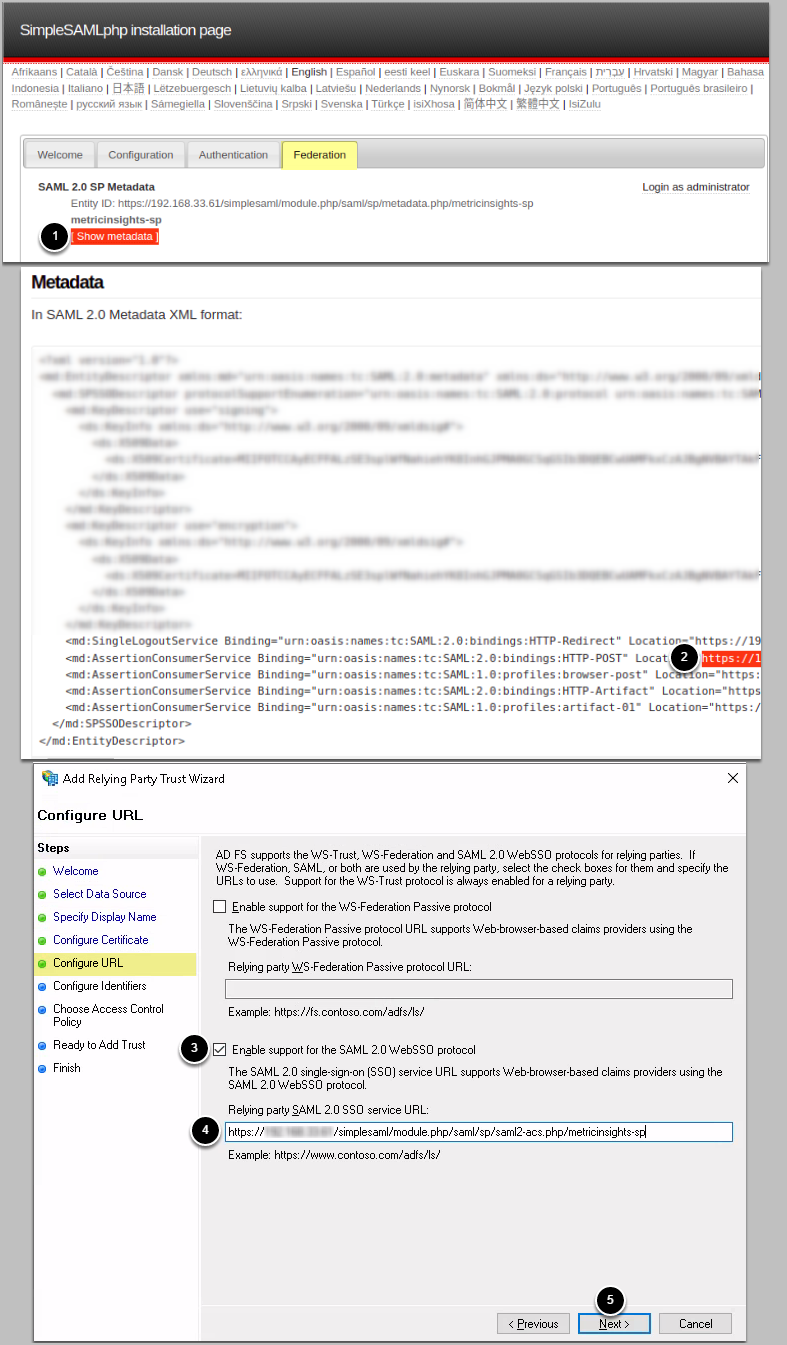
- From the Federation tab, click [Show metadata]
- Copy the location URL of HTTP-POST
- Select Enable support for the SAML 2.0 SSO Web SSO protocol
- Input the URL you copied from metadata
- Click [Next]
1.6. Configure URL
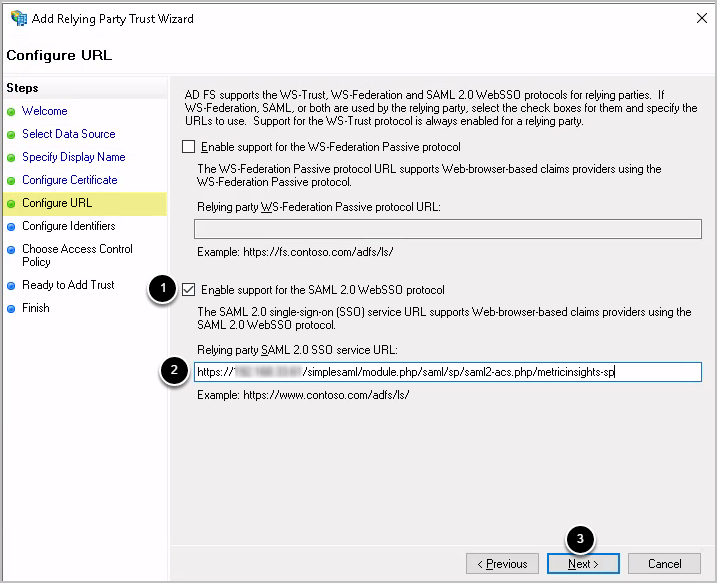
- Select Enable support for the SAML 2.0 SSO Web SSO protocol
- Input the URL you copied from metadata
- Click [Next]
1.7. Configure Identifiers
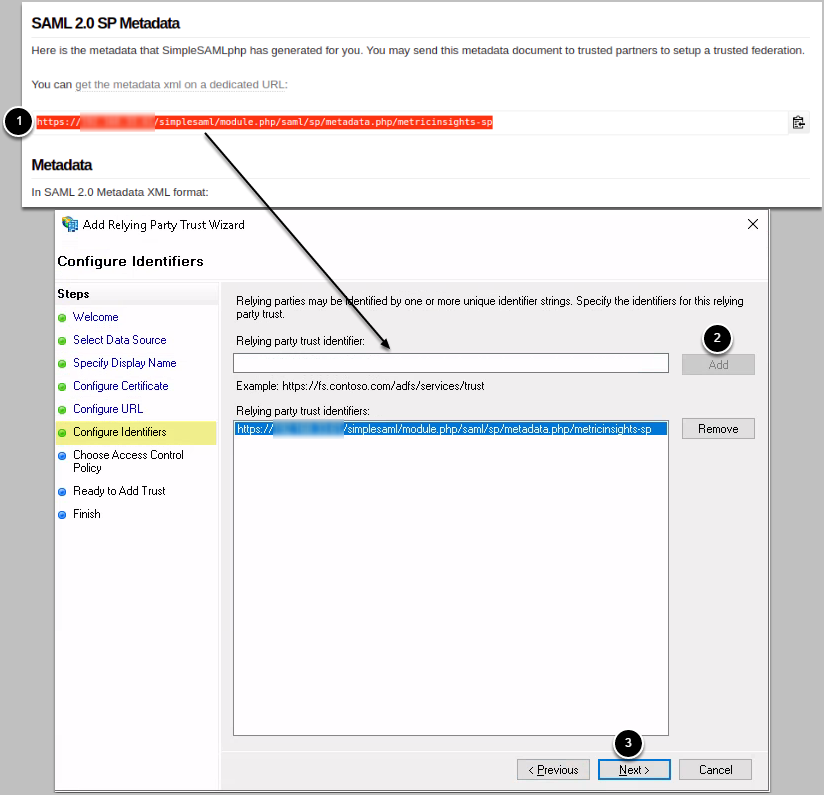
- Copy the Relying party trust identifier from the SAML 2.0 SP Metadata page
- Paste the identifier to Relying party trust identifier field and [Add]
- Click [Next]
1.8. Choose Access Control Policy
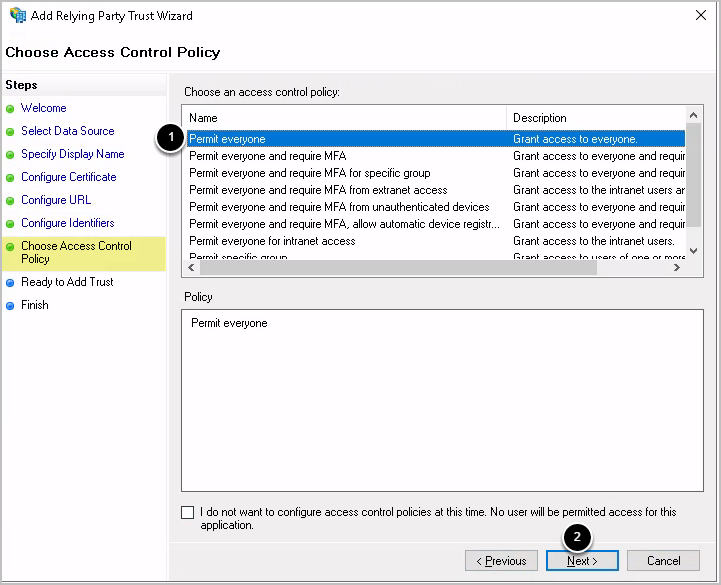
- If not selected by default, choose Permit everyone
- Click [Next]
1.9. Finish
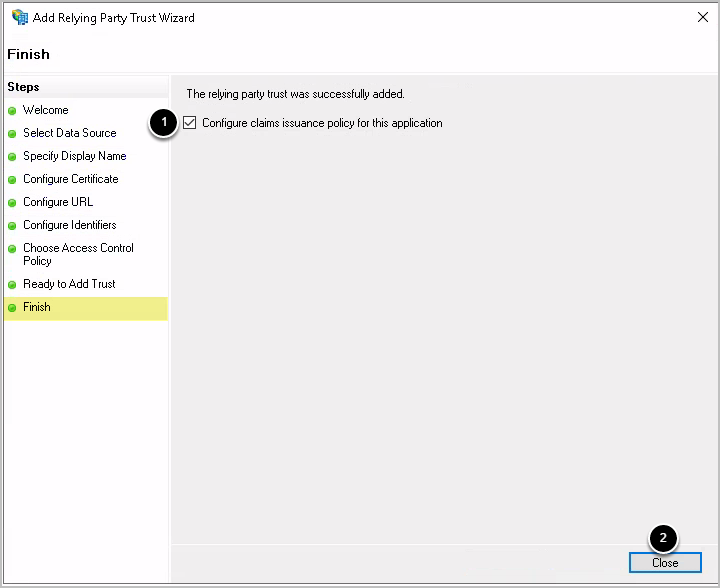
- Check Configure claims issuance policy for this application
- [Close]
2. Edit Claim Issuance Policy
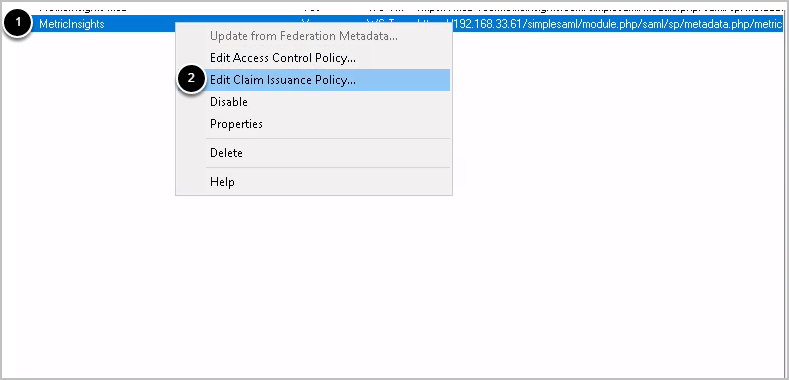
- Right-click the newly-added relying party
- Choose Edit Claim Issuance Policy and then click [Add rule]
2.1. Choose Rule Type
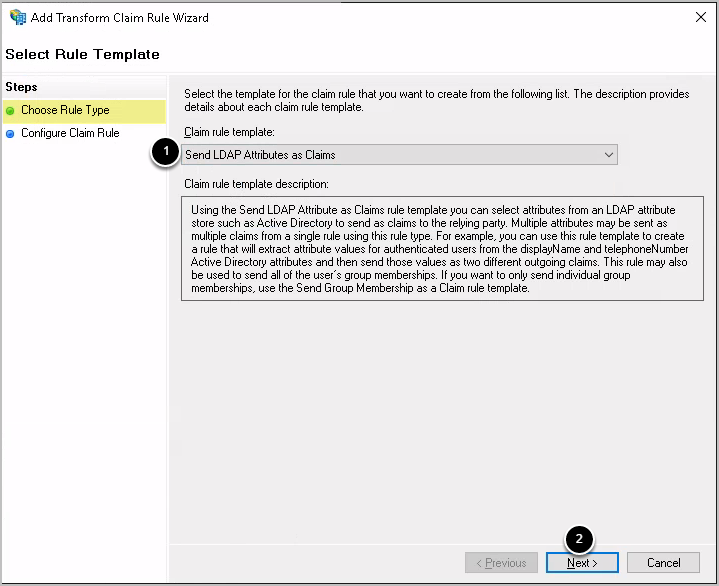
- Choose Send LDAP Attributes as Claims
- Click [Next]
2.2. Configure Claim Rule
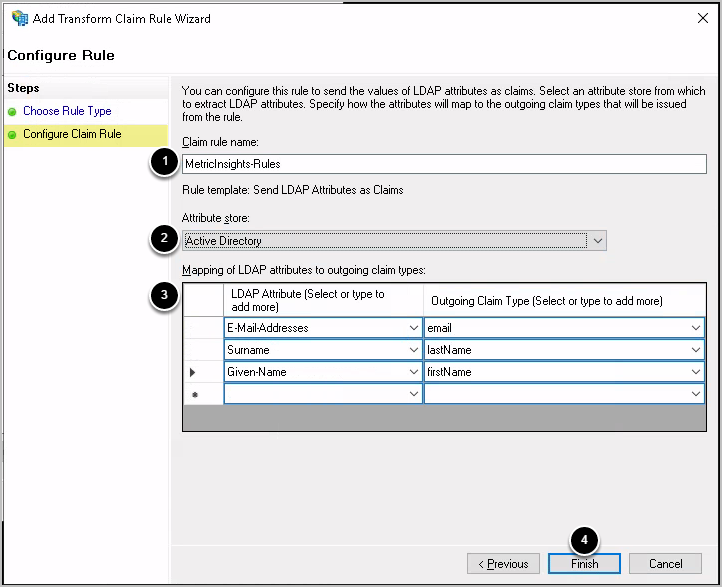
- Enter Claim rule name
- Set Attribute store to "Active Directory"
- Map LDAP Attributes
- [Finish]
Configuring the Application
- Get FederationMetadata.xml from ADFS by using:
- wget https://dc1.metricinsights.com/FederationMetadata/2007-06/FederationMetadata.xml, where https://dc1.metricinsights.com is the address of the ADFS server
- Parse the .xml file:
- In the web container, run the following command:
/opt/mi/iv/data/bin/mi-saml-config.php --input-file <full path to FederationMetadata.xml> --saml-type adfsv3 - The metadata from the response representing the DEFINE section to be copied to the /opt/mi/external_config/saml.php and /opt/mi/external_config/saml20-idp-remote.local.php files
- In the web container, run the following command:
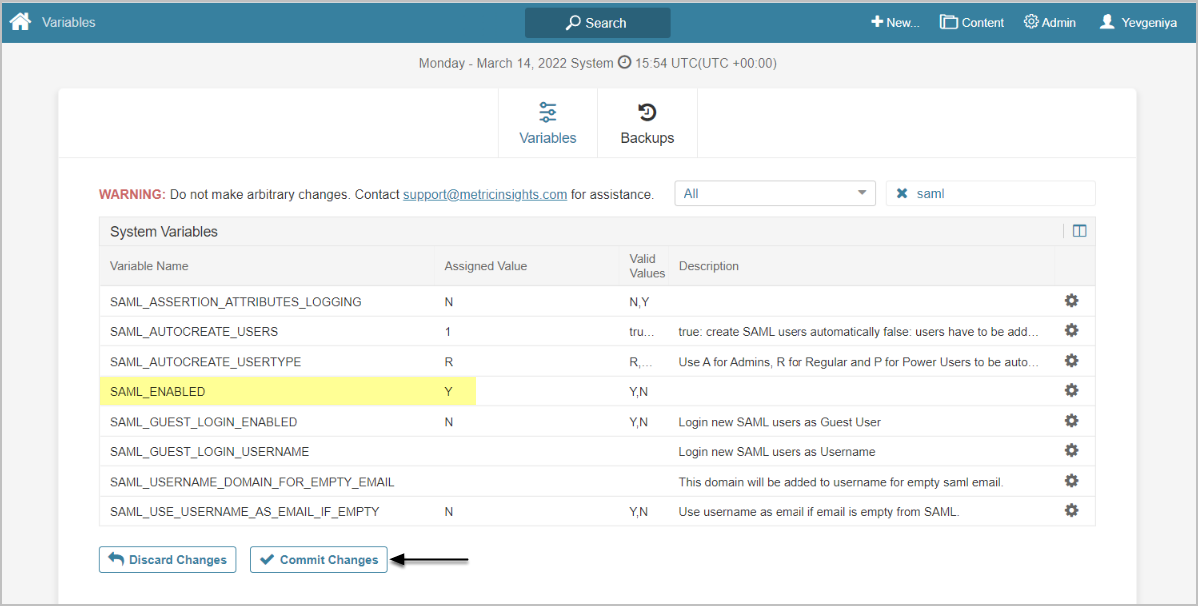
- Access Admin > System > System Variables, set SAML_ENABLED to 'Y', and [Commit Changes]. See the screen below.