The Lightweight Directory Access Protocol (LDAP) is an application protocol for accessing and maintaining distributed directory information services over an Internet Protocol network. LDAP user authentication validates a username/password combination against a directory server such as Active Directory or OpenLDAP.
With the Metric Insights LDAP integration, you can automatically create Metric Insights users based on existing user and group information in your LDAP server. Once configured, the integration greatly simplifies the setup of hundreds if not thousands of users.
Metric Insights LDAP integration currently supports the following features:
- Authenticate users against LDAP (If users change their passwords for other applications, the new password will also work to access Metric Insights)
- Automatically create Metric Insights users with user profile information from LDAP (e.g., first name, last name, email address, etc.)
- Automatically create Metric Insights groups that are mapped to LDAP groups and add users to those groups based on LDAP group membership
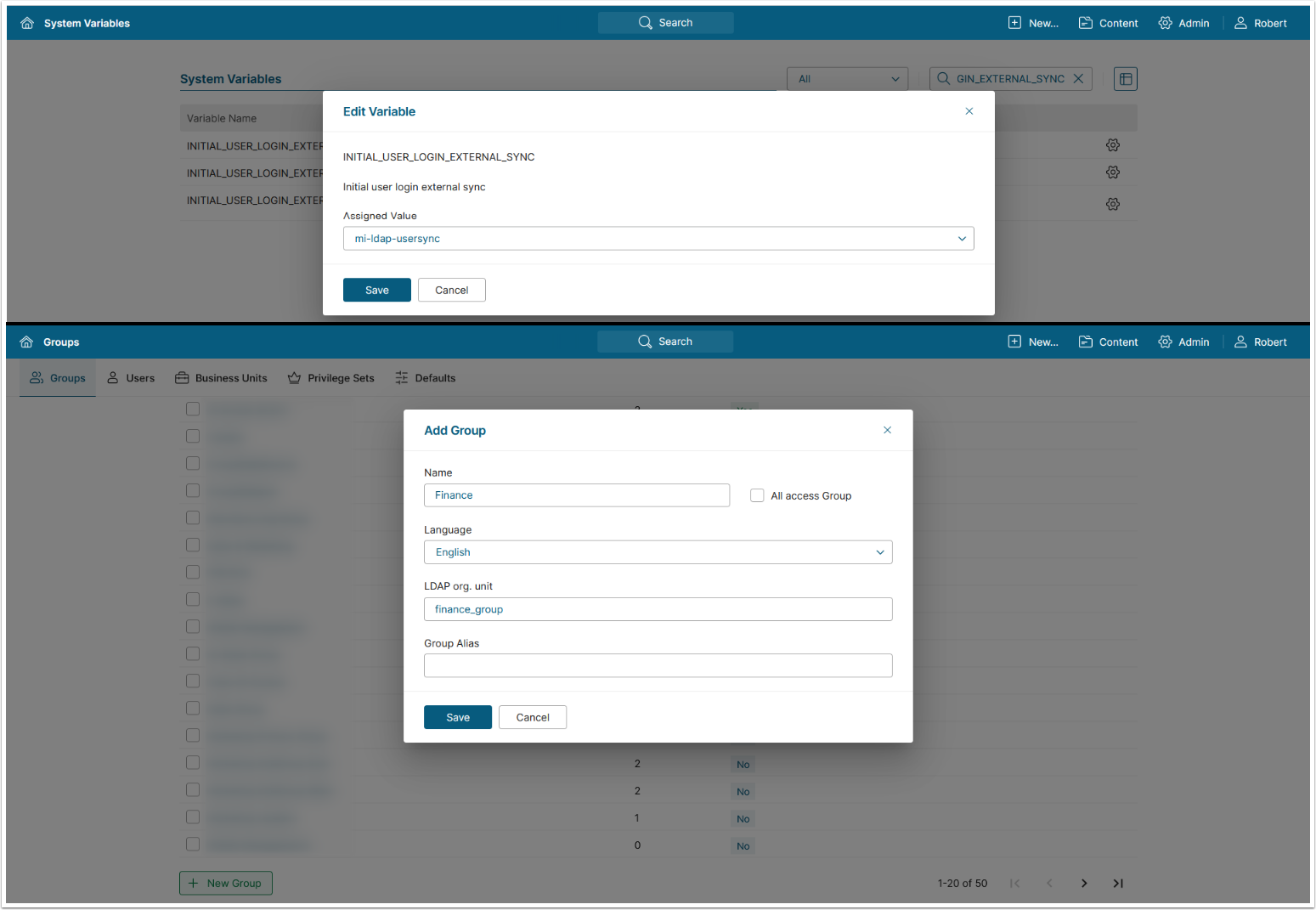
- For more details on automatically syncing users and groups, see mi-ldap-usersync.
- NOTE: Beginning v7.0.2 LDAP User Sync can be configured via MI Console, see Configure User Sync with MI Console for details.
- For more details on automatically syncing users and groups, see mi-ldap-usersync.
- Automatically sync user profile information on successful login
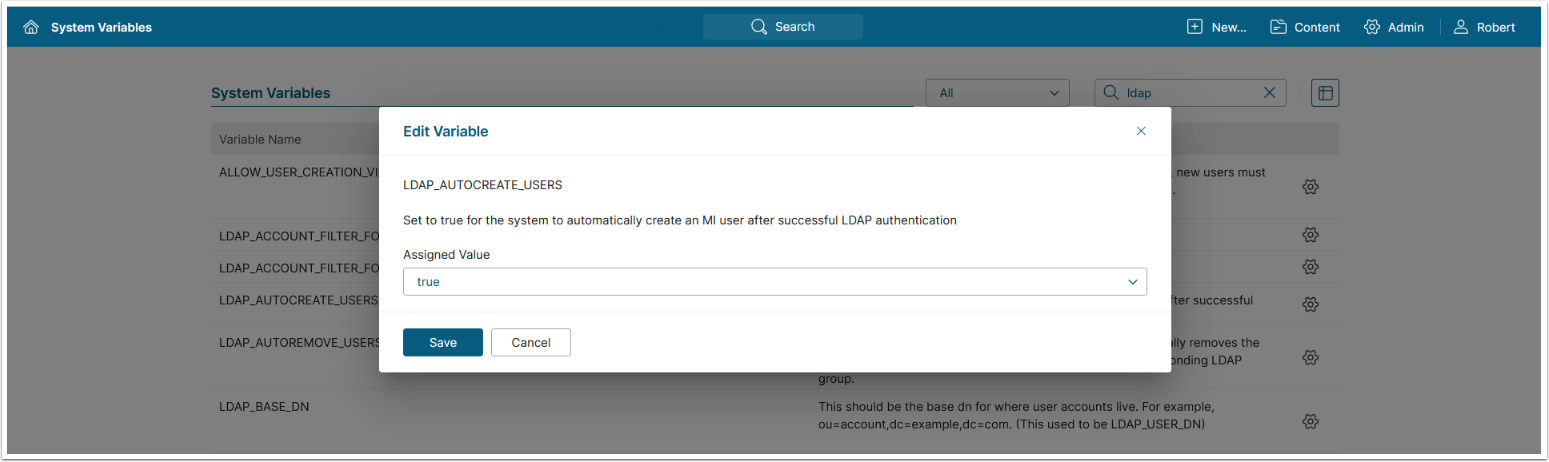
- Auto-creation of LDAP users can be selectively turned on or off
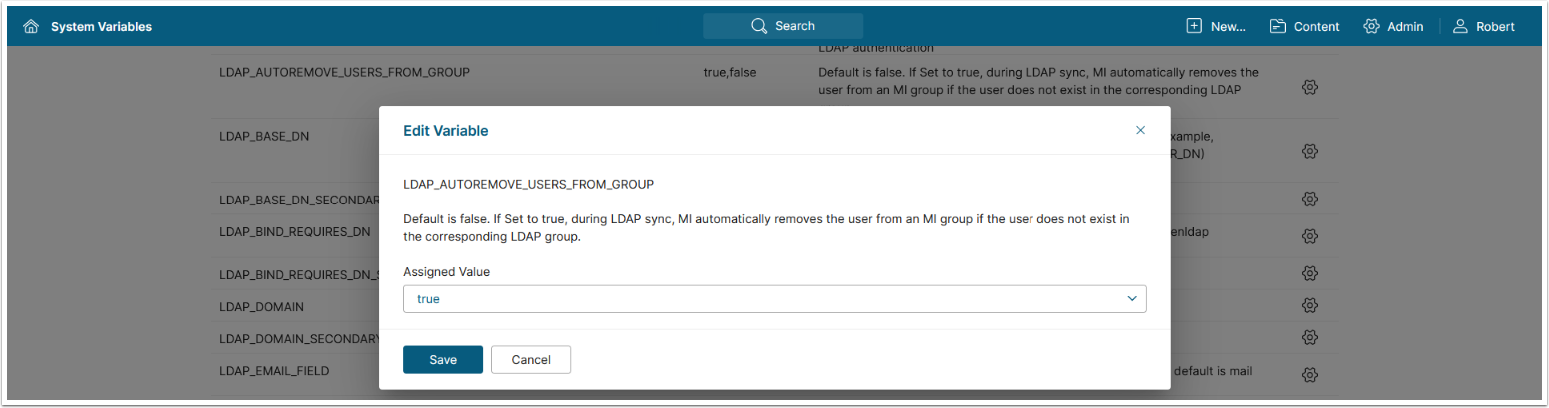
- Auto-remove users from MI groups based on LDAP group membership
To read more about configuring this integration, see Configuring LDAP Authentication.
Table of contents:
Metric Insights LDAP integration requires the following ports to be open:
- LDAP: TCP 389
- LDAPS: TCP 636
The LDAP authentication mechanism can query against any Active Directory service that supports the LDAP/S protocol, including Microsoft Active Directory.
NOTE: Check the connectivity between MI and LDAP server from the web container: mi-support telnet --address <ldap.server.address> --port 389 -v
1. Basic Use Case
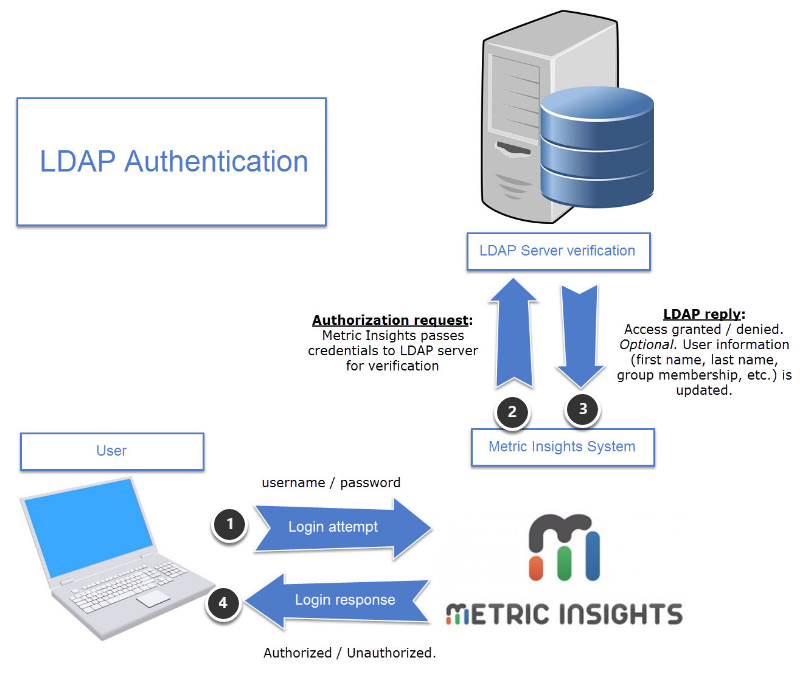
The process is as follows:
- User enters credentials on the Metric Insights login page.
- Metric Insights passes credentials to the configured LDAP/Active Directory service.
- LDAP verifies that the user is authorized. In the event the user profile does not yet exist in Metric Insights, the user profile is automatically created based on the LDAP user data (first name, last name, email address). If any existing user information has changed on the LDAP server since a prior authentication, that information is automatically updated in Metric Insights.
- On successful authentication, the user is logged into Metric Insights.
2. Use Case for New Users (Real-Time Group Sync)
NOTE: User Group membership assignment on initial login is controlled by the System Variable INITIAL_USER_LOGIN_EXTERNAL_SYNC. Disabled by default.
The available options are:
- mi-ldap-usersync/mi-o365-usersync: References LDAP/Office 365 to identify the User’s Groups and assigns the User to corresponding Groups in Metric Insights.
- Custom Script: Assigns Group membership based on a User Access Dataset tied to a Custom Script.
- Admin creates Groups in Metric Insights and maps them to LDAP "organizational units" (i.e., groups).
- New user enters credentials into Metric Insights.
- Metric Insights passes credentials to the configured LDAP/Active Directory service.
- LDAP verifies that the user is authorized.
- User is logged into Metric Insights.
- Metric Insights obtains information about the new user from the LDAP server, including name, email, and LDAP group assignments.
- Metric Insights will assign the new user to all groups that are mapped to LDAP organizational units
Example: Metric Insights' Finance group is mapped to LDAP organizational unit finance_group. A new user is a member of this LDAP organizational unit finance_group, so Metric Insights assigns the user to the Metric Insights Finance group. If applicable, Metric Insights will assign the user to multiple groups in the application.
3. Use Case for Users That Change Groups
An Administrator can establish optional configuration parameters to auto-remove users from MI groups based upon LDAP group membership.
NOTE: See Configuring LDAP Authentication for more details on LDAP configuration parameters.
4. Optional Settings for New Users
An Admin can set an optional configuration parameter that will prevent new user accounts from being created automatically. This permits LDAP/Active Directory integration while giving Administrators direct control over the creation of new user accounts.
NOTE: See Configuring LDAP Authentication for more details on LDAP configuration parameters.