For Microsoft SharePoint Plugin, to successfully connect to Microsoft SharePoint Online:
- Application must be registered on Microsoft Azure Portal
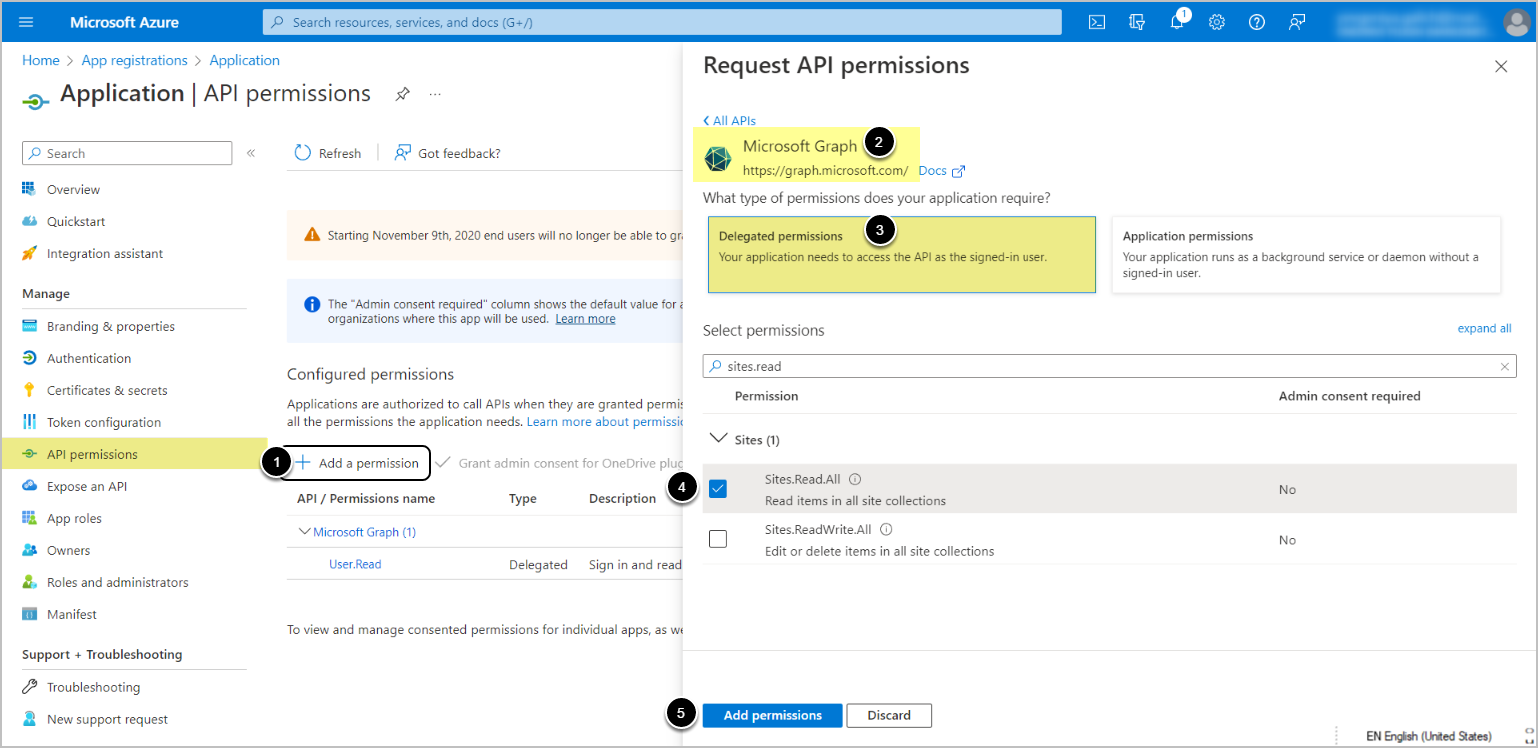
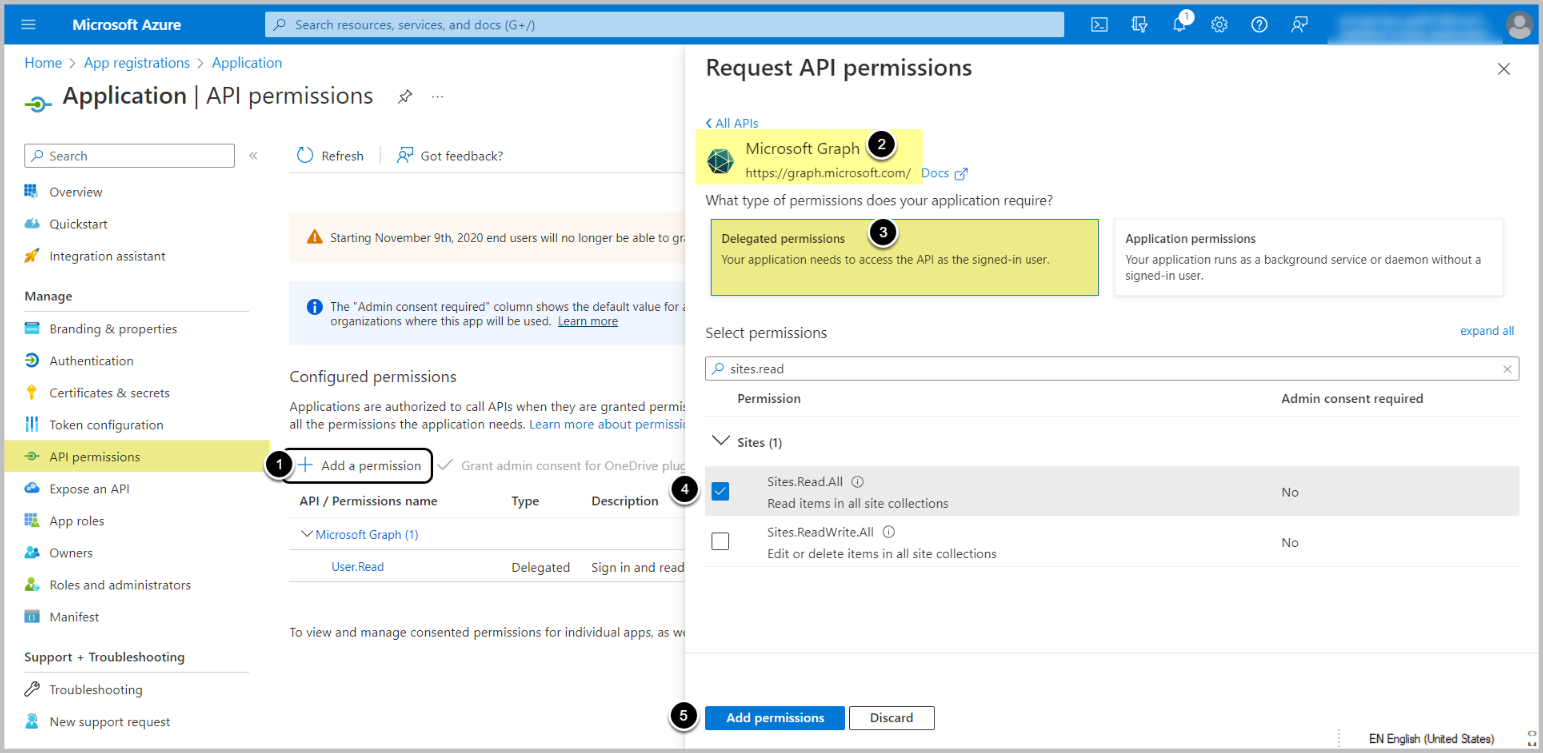
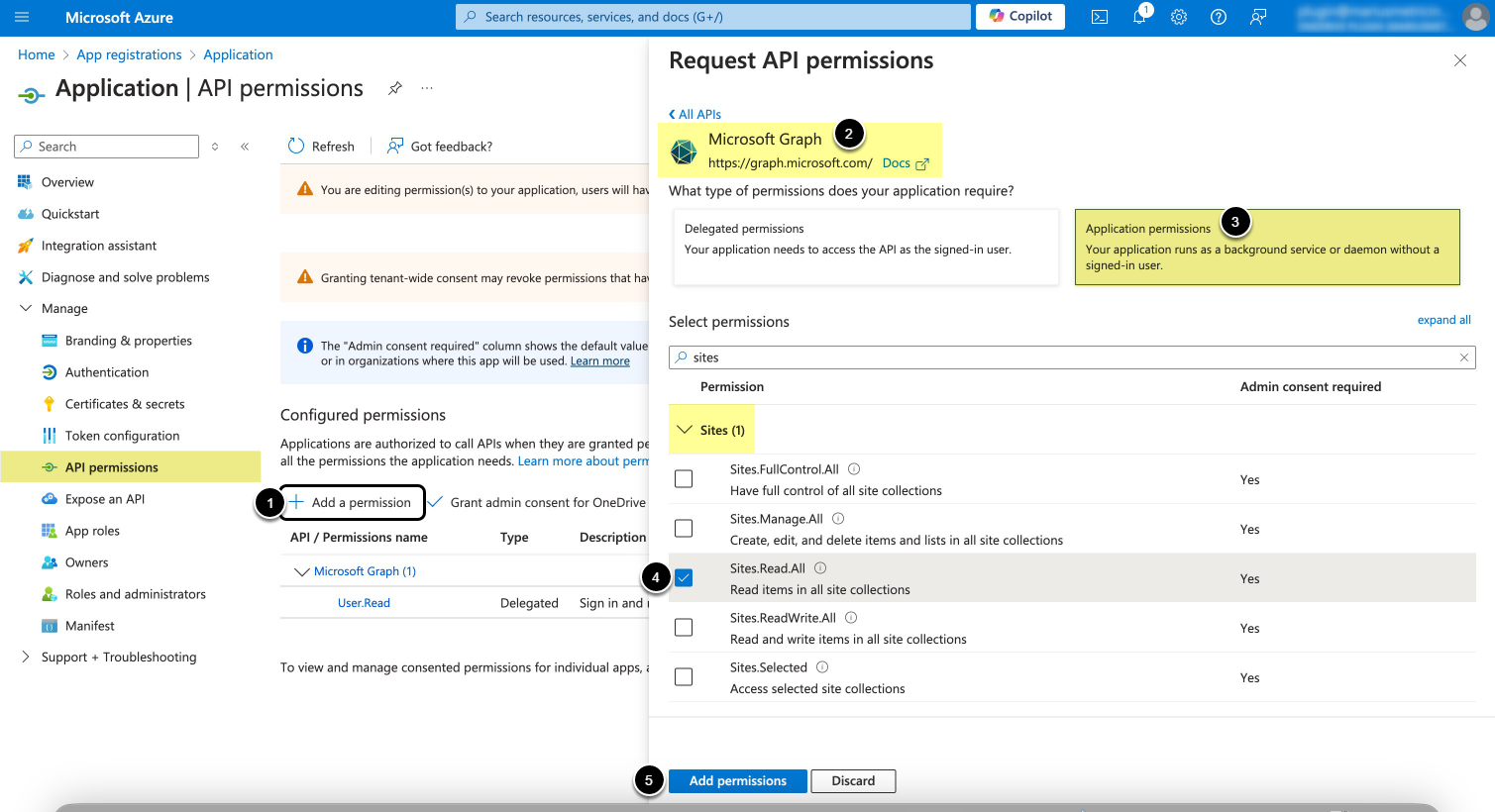
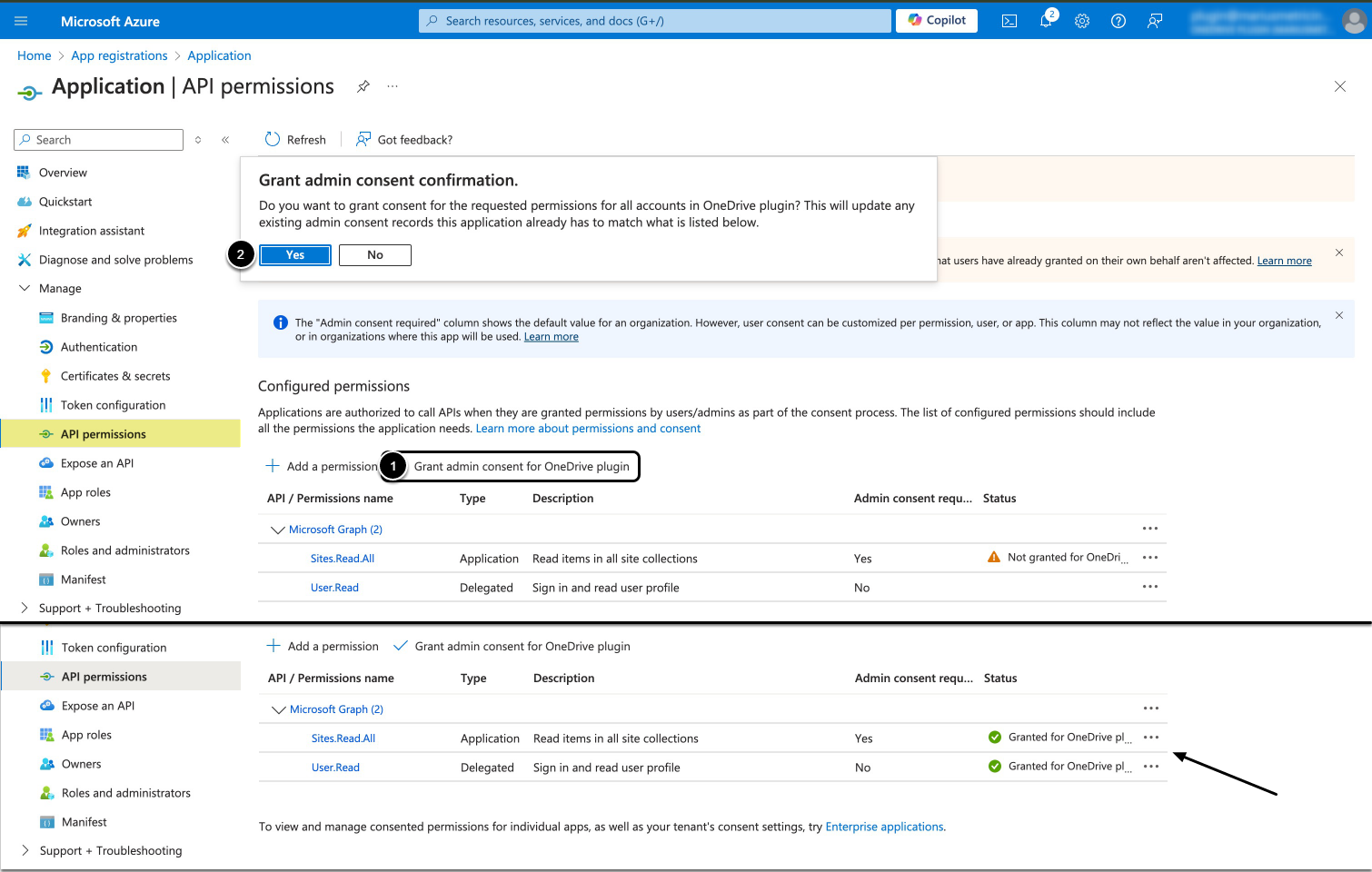
- API access must be enabled for the application on Microsoft Azure Portal depending on Auth Type:
- For Password/OAuth – Delegated Permissions. NOTE: Password Auth has been deprecated in v7.1.2.
- For Client credential – Application permissions
Additionally:
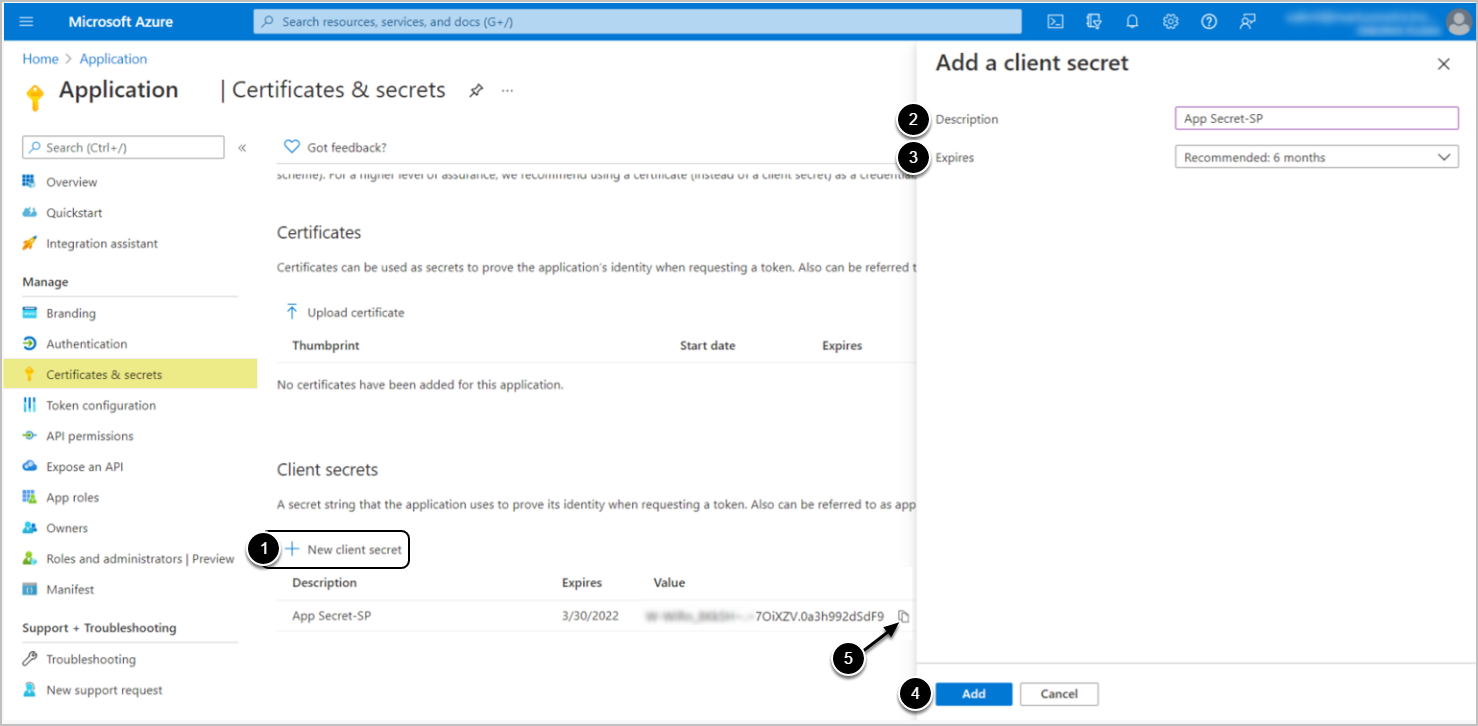
- Client credential requires generating Client Secret
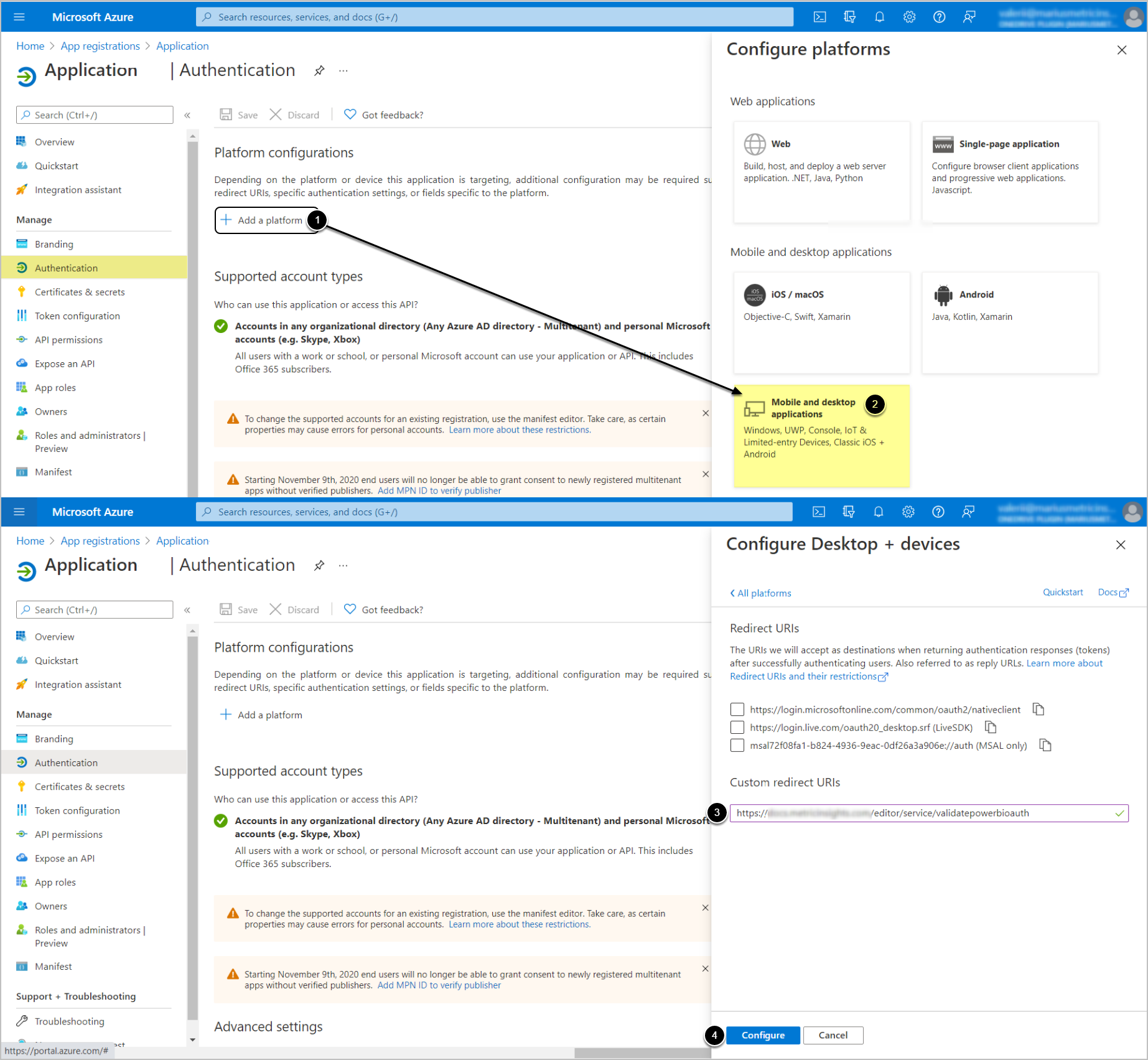
- OAuth requires adding redirect URIs
Start by registering an application and proceed depending on the Auth Type to be used:
- Password [DEPRECATED IN 7.1.2]
- OAuth
-
Client Credential
- [Only for retrieving SharePoint Group Membership Dataset] Certificate Auth
- Identity Profile
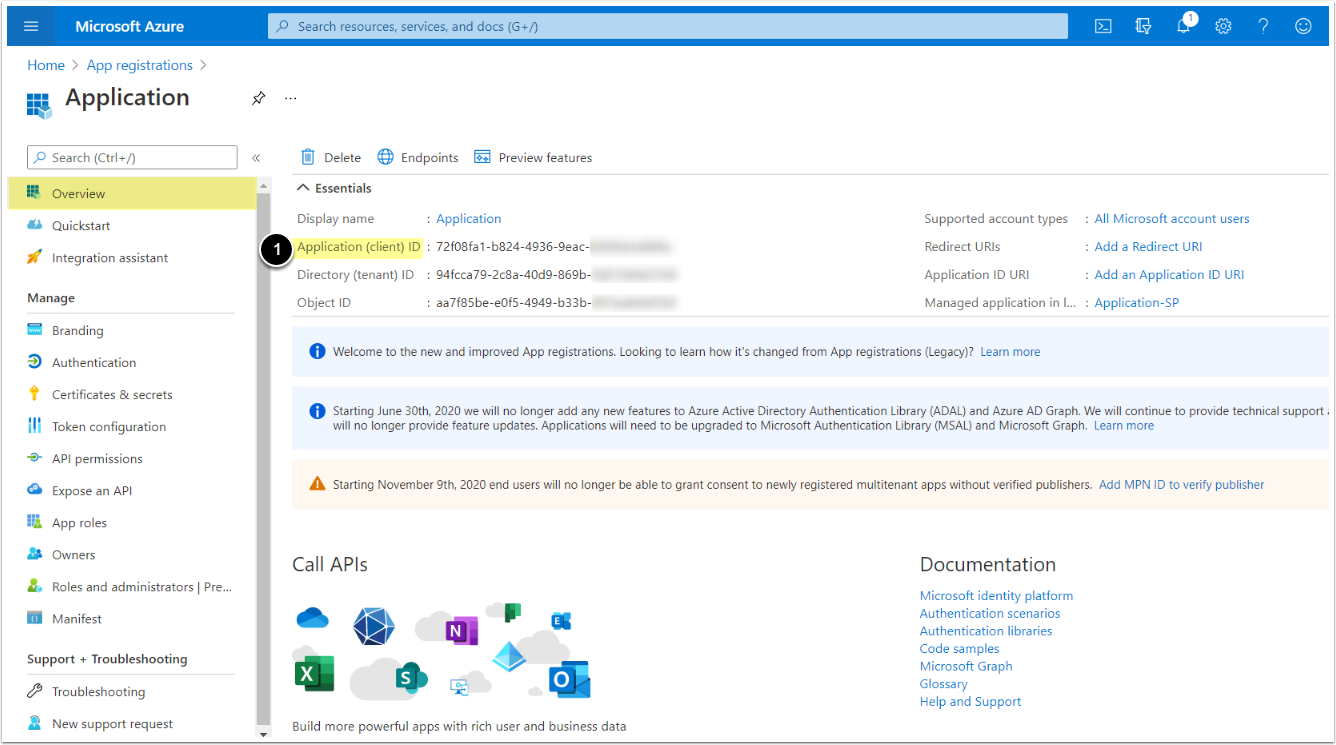
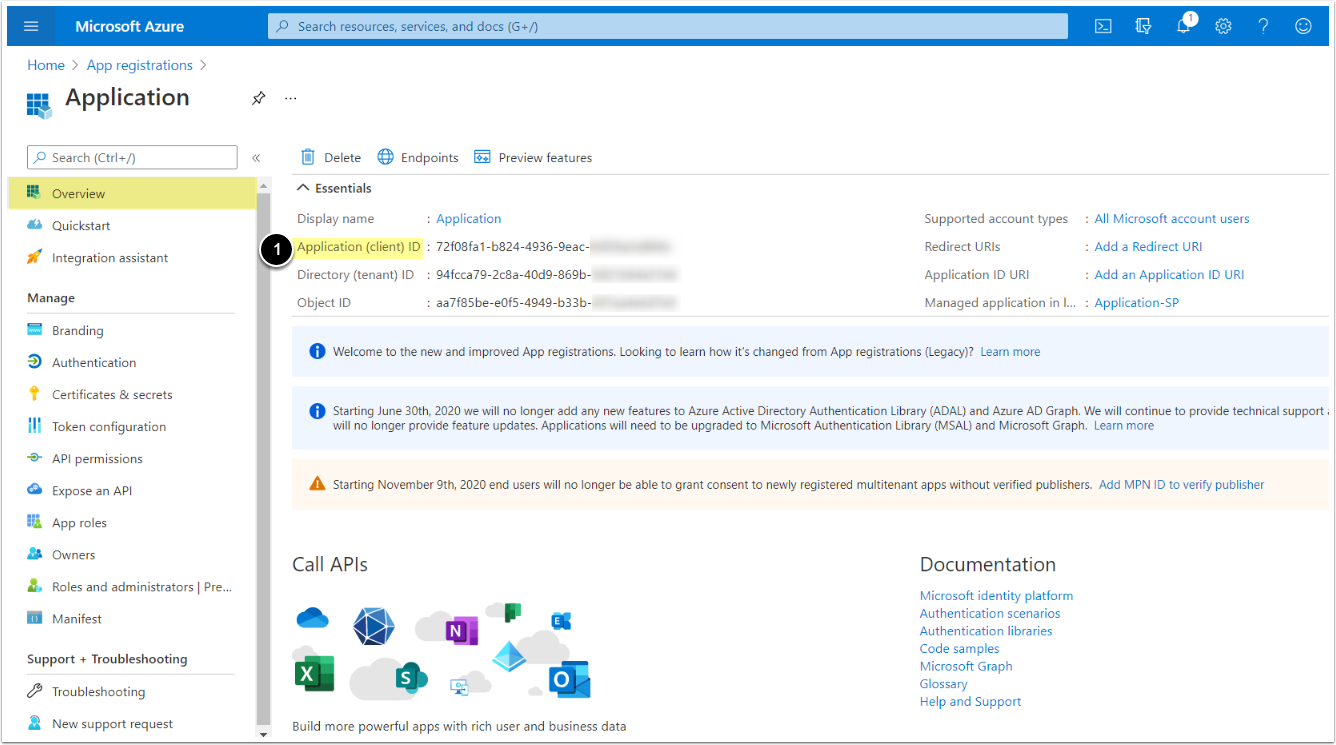
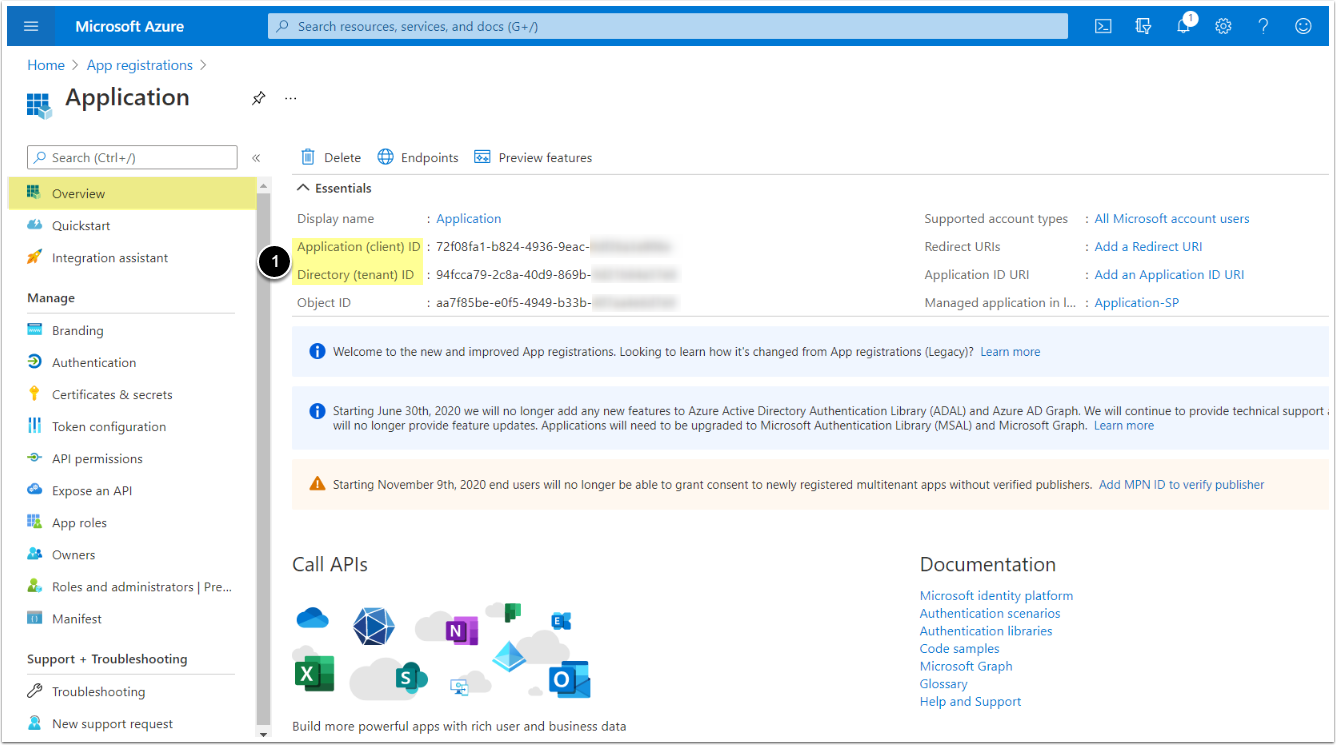
1. Register an Application
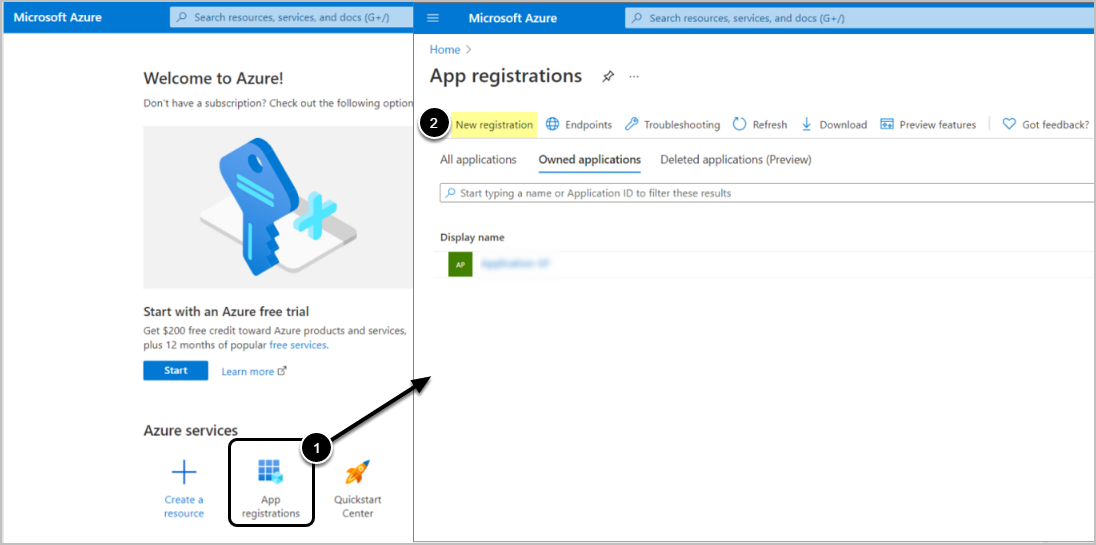
Access Azure Portal's Home
- Select App registrations
- Proceed with New registration
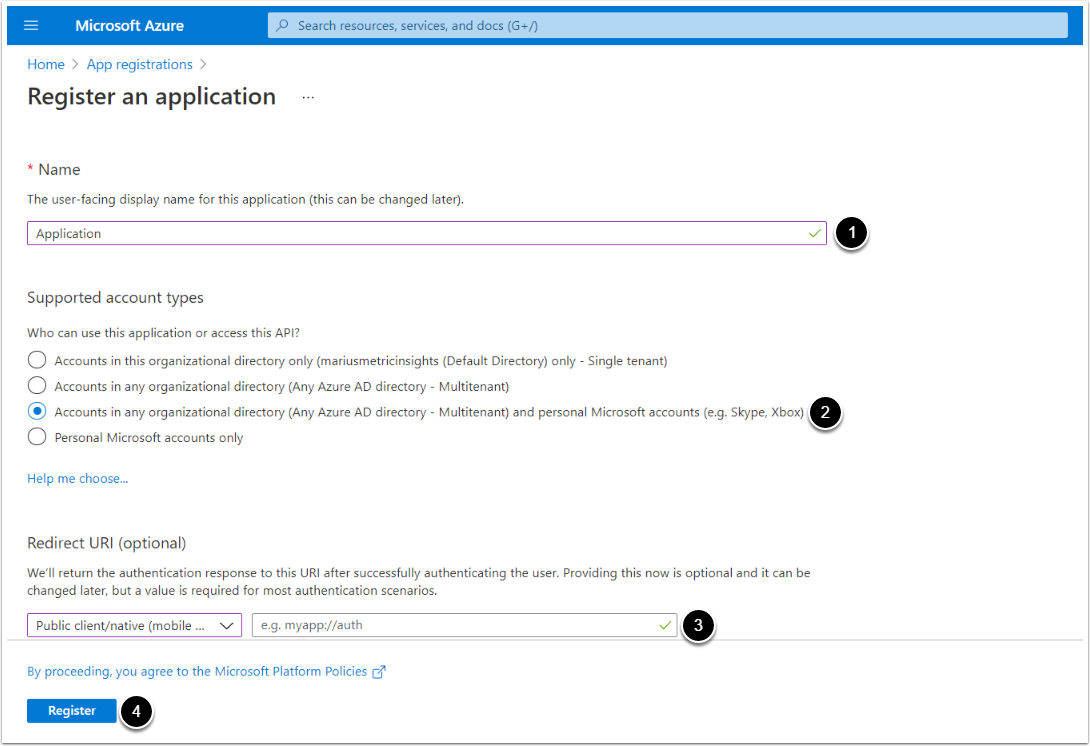
- Input a descriptive phrase in Name
- Specify Supported account types as shown on the screen
- Setting the value for Redirect URI is required only for OAuth, but can be done later. See the OAuth section for instructions.